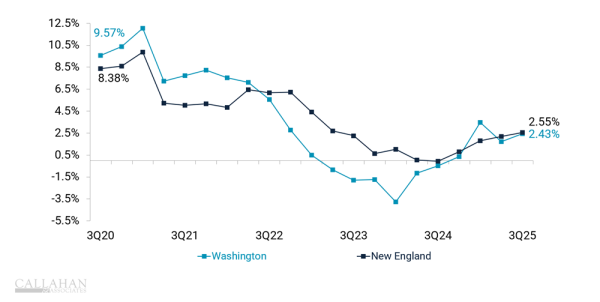
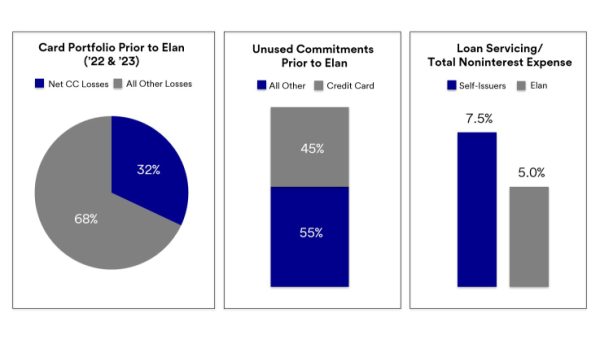
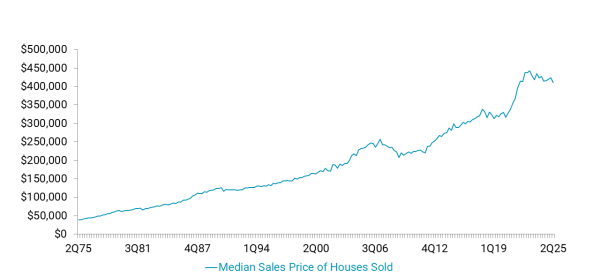
Digital Account Opening: Removing Friction and Enhancing the Member Experience
Having a digital onboarding experience that reduces friction and simplifies the account opening process is essential. Join us as Baron Conway (svp, head of digital and non-branch experiences at Nuvision Federal Credit Union, $2.7B) and Courtney Rowan, vp, digital experience at Citadel Credit Union, $4.4B) discuss how they have taken on digital transformation and looked